Bloomio Security Challenge
(closed)Update as of 16th of Jan 2020 — The challenge has finished the 15th of Jan, 2020 at 00:00 CET. No security gap has been identified and none of the 3 challenges have been solved.
Bloomio puts the security of its customer at the first place, this is why we decided to offer a monetary compensation to anyone who will find a security gap in our current development.
Bloomio’s challenge programme supports the reporting and quick elimination of security gaps in our product ahead of its commercial launch.
3 security challenges have been formulated and a reward is associated to each of these challenges.
The Challenges
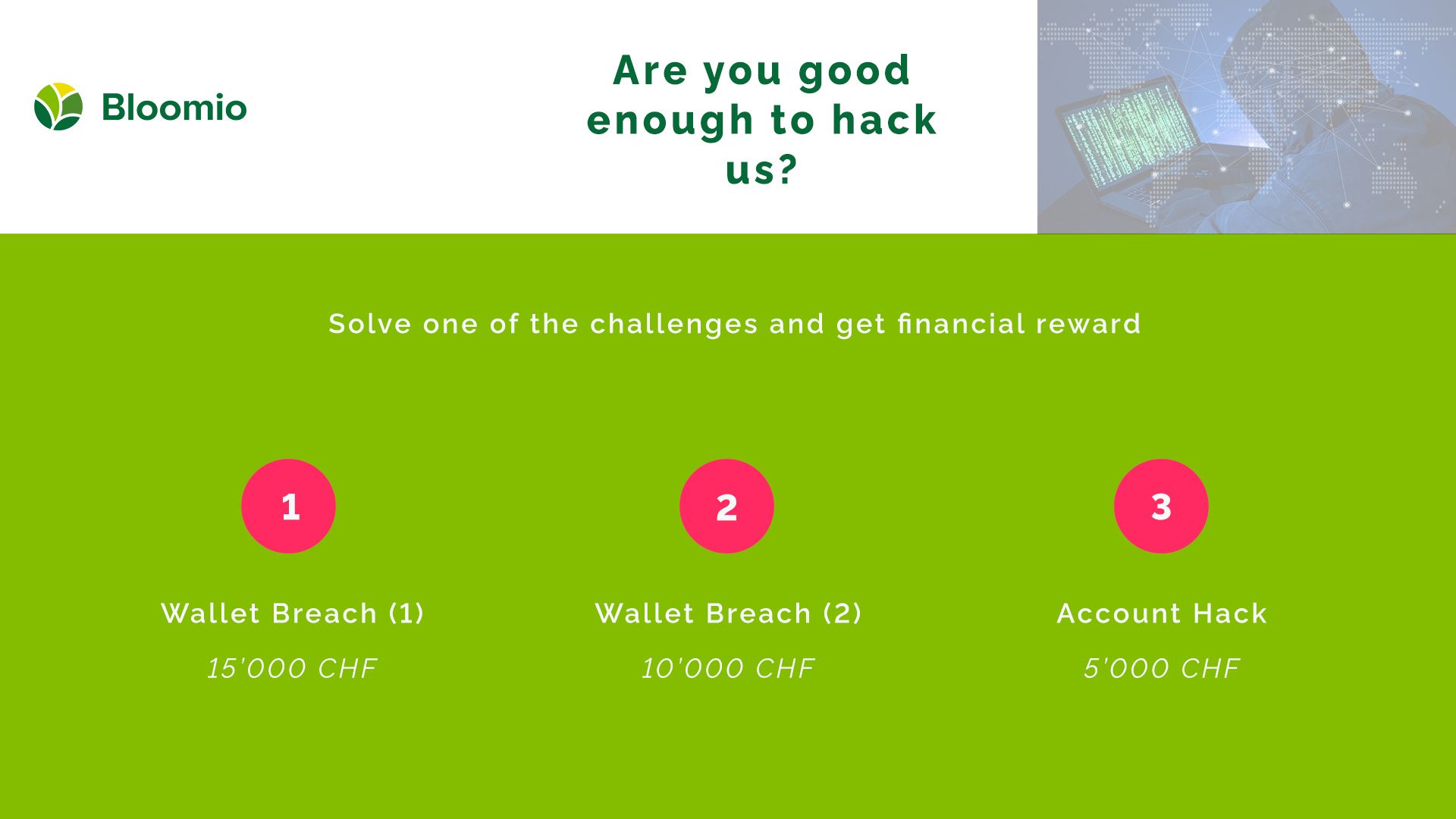
- Transfer 100 Demo euro coins from the defined “wallet” to any “wallet” outside Bloomio universe. Reward: 15'000 CHF
- Transfer 100 Demo euro coins from the defined “wallet” to another “wallet” inside Bloomio universe. Reward: 10'000 CHF
- Access the account and change personal data of the Bloomio account of the corresponding defined “wallet”. Reward: 5'000 CHF
Who is it for?
Both private individuals and organisations can participate in the challenge and identify security gaps to be reported to Bloomio’s development team.
Conditions and reward eligibility:
Timing: All the 3 mentioned challenges will remain active until the 15th of Jan, 2020 at 00:00 CET
Scope: The challenge only refers to the above 3 challenges and no-stress tests or cause of Denial-of-services are in scope at this stage.
Rewards: Each challenge is independent of the other 3 and solutions to each single challenge can be proposed independently of the others. Only the first solver of each challenge will be eligible for the above defined rewards. In case a challenge will be solved, Bloomio will communicate within 24 hours from the receiving of the solution proof, that the challenge is not any longer active. Related communications will be done on this page.
Confidentiality: The participant in the challenge agrees that, in the case a solution to the challenge will be found, details of the vulnerability will not be shared beyond Bloomio team for 6 months.
Submission: An email with the proposed solution to the challenge should be sent to
The email should contain the following information:
- specification of which challenge has been solved
- proof of completion
- detailed description of the vulnerability and steps put in place to achieve bypass Bloomio’s security
- contact details